When Your Windows Machine Loses Trust - A Deep Dive into Domain Relationship Issues
When one door of happiness closes, another opens. - Helen Keller
When Your Windows Machine Loses Trust: A Deep Dive into Domain Relationship Issues
“Trust takes years to build, seconds to break, and forever to repair.” - Unknown
Picture this: It’s Monday morning, and Sarah, a senior developer, arrives at the office ready to tackle her project deadlines. She boots up her workstation, enters her credentials as usual, but instead of being greeted by her familiar desktop, she’s met with an enigmatic error: “The trust relationship between this workstation and the primary domain failed.” Her heart sinks. We’ve all been there, haven’t we?
Here are screenshot of the errors:
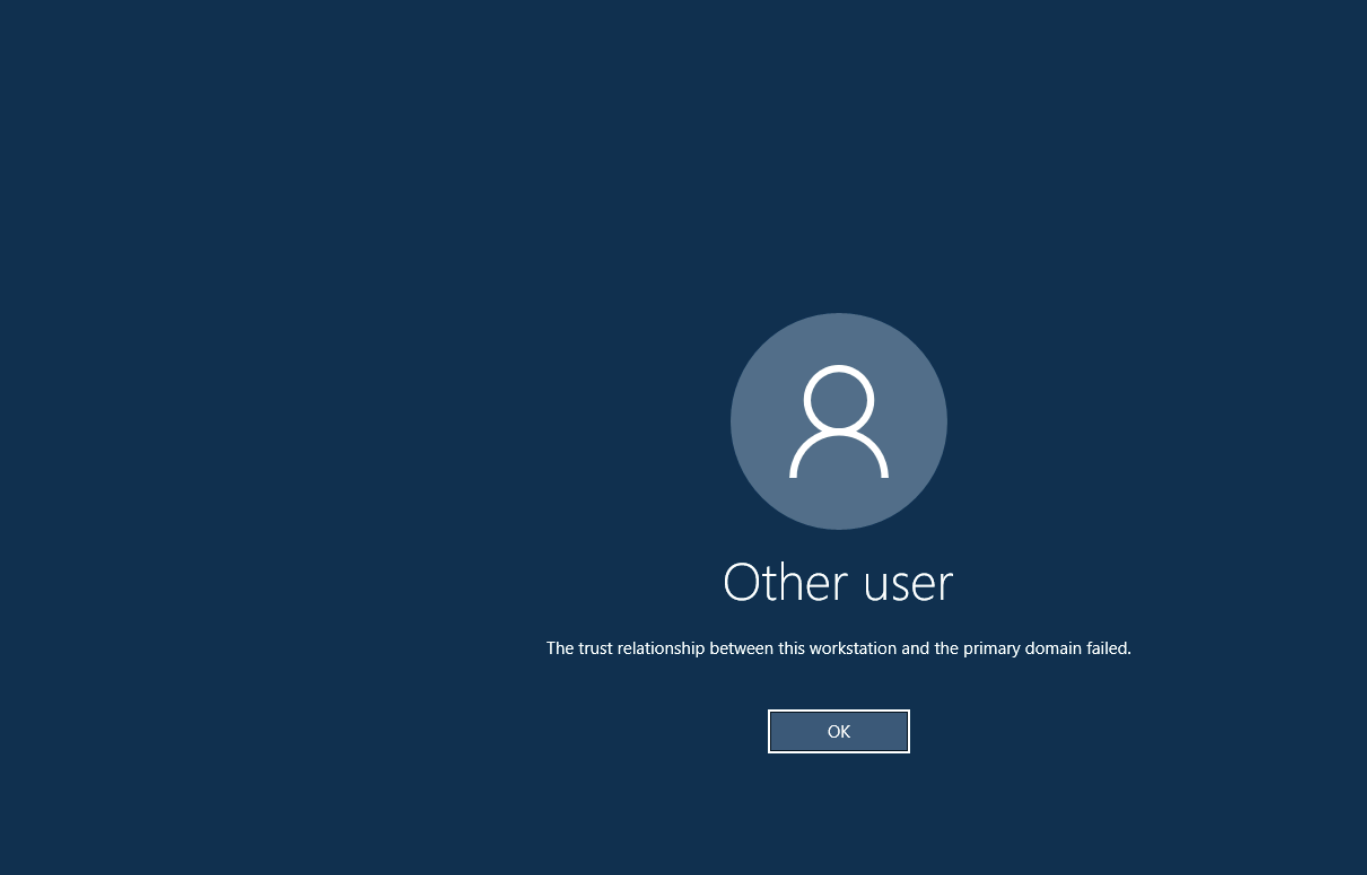
and
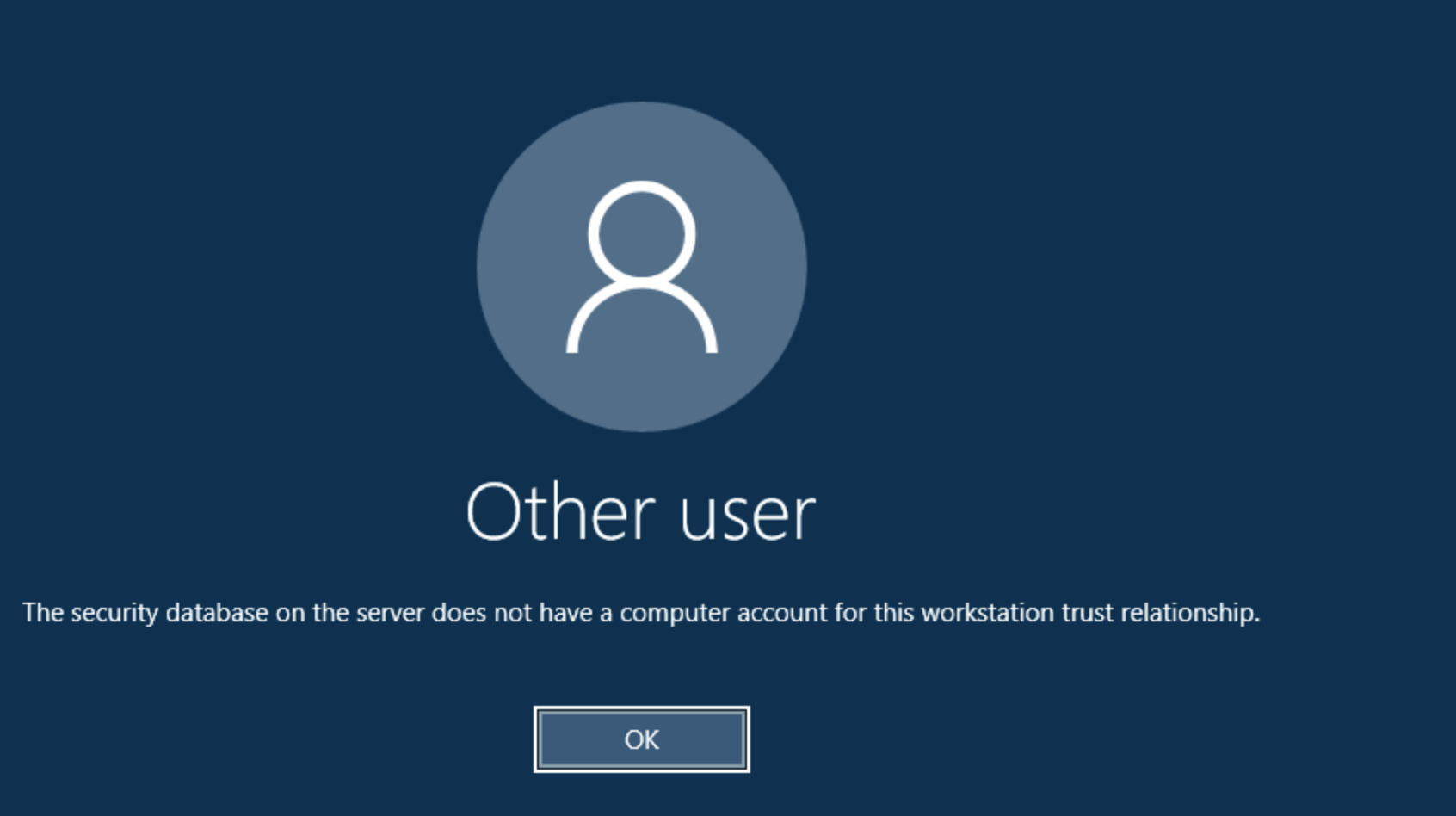
The Trust Crisis: Understanding Domain Relationship Failures
Just like any relationship, the bond between your Windows machine and its domain controller is built on trust. When this trust breaks, it’s like a digital divorce – messy, frustrating, and in need of immediate intervention. But fear not! This comprehensive guide will walk you through understanding, fixing, and preventing these trust relationship failures.
The Heart of the Matter: What’s Really Going Wrong?
Imagine your computer and the domain controller as two dance partners. They need to stay in perfect sync, following the same rhythm (timestamps). When one partner starts following a different beat, the dance falls apart. This is exactly what happens when the local machine and LDAP domain controller fall out of sync.
The Quick Fix: Getting Back on Your Feet
Before we dive into the deeper technical aspects, let’s address the immediate solution. Think of it as the equivalent of turning off your TV and turning it back on – except a bit more sophisticated:
- Log in using your local admin credentials (your backup key to the kingdom)
- Temporarily move your machine to a workgroup (like taking a break from the relationship)
- Restart your computer (the classic “take a breather” approach)
- Rejoin the domain (reconciliation time!)
As below screenshot
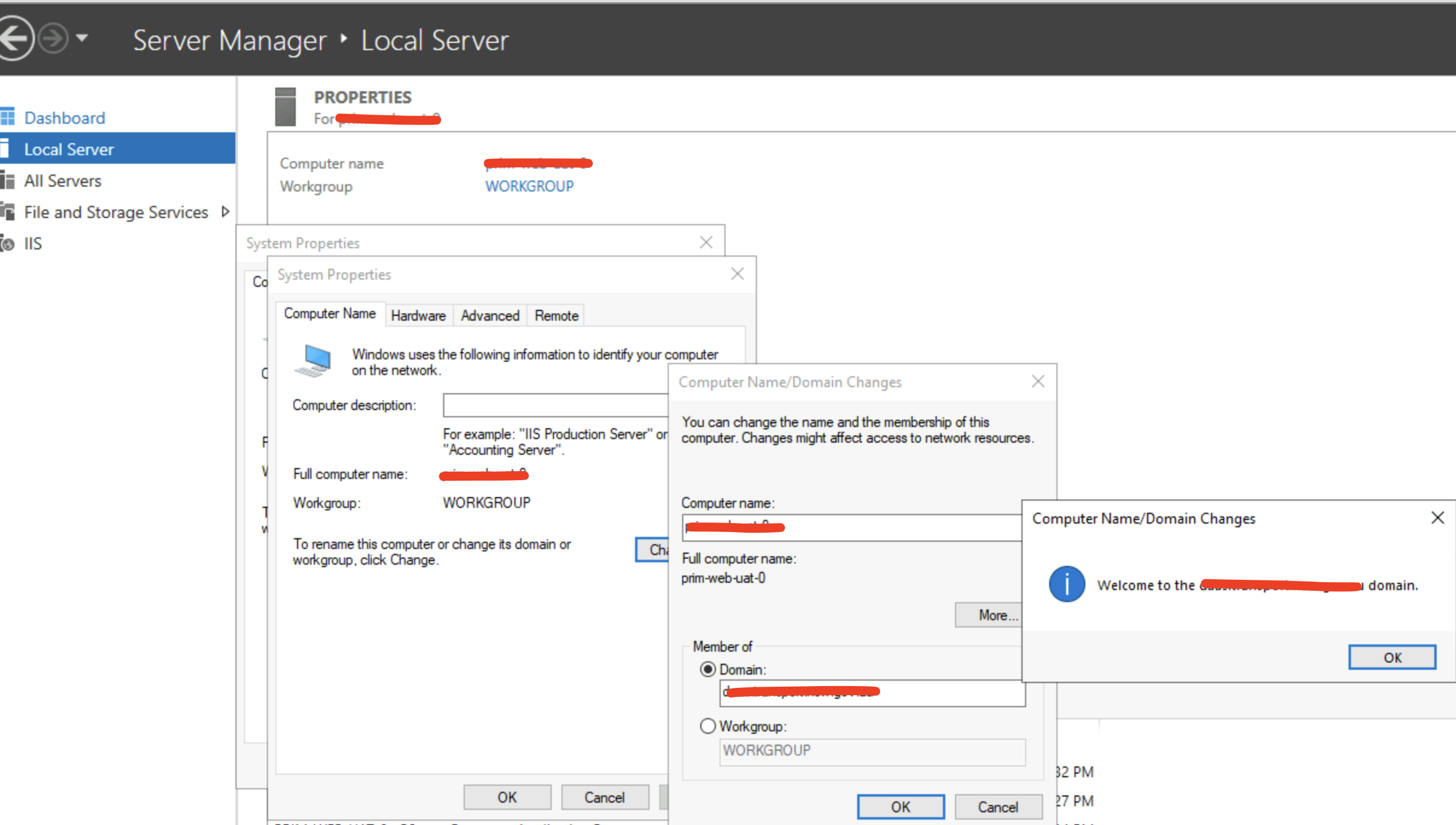
Generallly, you go to “Local Server”, change the domain to “Workgroup”, and restart the computer.
Pro tip: If your machine plays hard to get during the rejoin process, you might need to remove the computer account from the domain controller first. It’s like clearing the air before starting fresh.
Just like below error:
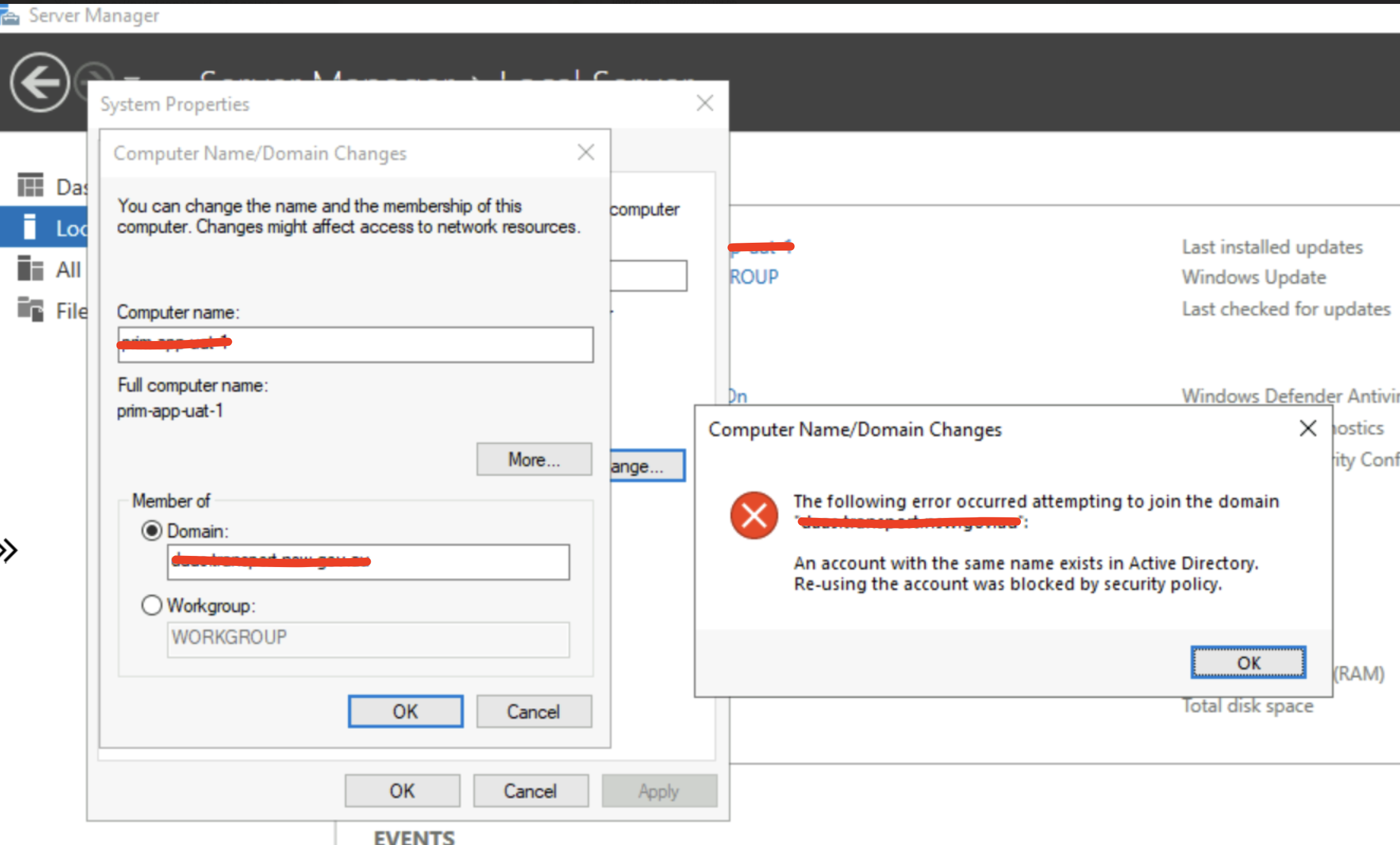
The Detective Work: Understanding the Root Cause
Here’s where it gets interesting. Like any good relationship counselor, we need to understand what went wrong by examining both sides of the story. We’ll use two powerful scripts to investigate:
Local Check Script (local_check.ps1)
To run below script which is to collect the password last set value LSA secrets of the computer:
- Log on with local administrator, download and copy psexec.exe (from Microsoft website) and the local_check.ps1 script into your VM local disk.
- Open an elevated command prompt, switch to SYSTEM context, and call the script by running (Please change the path accordingly):
.\psexec.exe -i -s powershell -ExecutionPolicy Bypass -Command GetSecret_CupdTime_from_stale_comp.ps1
Below is the script examines your local machine’s timestamp – think of it as checking your computer’s personal diary.
Script for GetSecret_CupdTime_from_stale_comp.ps1:
# get local LSA Secrets modification date from registry
$LSAsecret = Get-Item -Path 'Registry::HKEY_LOCAL_MACHINE\SECURITY\Policy\Secrets\$MACHINE.ACC\CupdTime'
$REGkeyCupdTime = reg.exe query $LSAsecret /ve
$r = $REGkeyCupdTime[2]
$CupdTime= $r.split(" ")
$CupdTimevalue =$CupdTime[$CupdTime.Length-1].trim()
$CupdTimevalueNew = $CupdTimevalue.Substring($CupdTimevalue.Length -2,2) + $CupdTimevalue.Substring($CupdTimevalue.Length -4,2) + $CupdTimevalue.Substring($CupdTimevalue.Length -6,2) + $CupdTimevalue.Substring($CupdTimevalue.Length -8,2) + $CupdTimevalue.Substring($CupdTimevalue.Length -10,2) + $CupdTimevalue.Substring($CupdTimevalue.Length -12,2) + $CupdTimevalue.Substring($CupdTimevalue.Length -14,2) + $CupdTimevalue.Substring($CupdTimevalue.Length -16,2)
# convert to utc time format
$LastPasswordUpdateTime = ([datetime]::FromFileTimeUTC([Convert]::ToInt64($CupdTimevalueNew,16))).ToString("yyyy-MM-dd hh:mm:ss")
# print to screen and save to file (change path if needed)
Write-Host -NoNewline "Password Last Set Time(UTC) in the Local Machine secrets LSA`t: "
Write-Host -ForegroundColor Green $LastPasswordUpdateTime
Set-Content -Path "c:\temp\GetSecret_CupdTime_from_stale_comp.txt" -Value ("Password Last Set Time(UTC) in the Local Machine secrets LSA " + $LastPasswordUpdateTime)
Write-Host -NoNewLine 'Press any key to continue...';
$null = $Host.UI.RawUI.ReadKey('NoEcho,IncludeKeyDown');
LDAP Check Script (ldap_check.ps1)
Here is another script to collect the pwdlastset attribute of the computer AD account object by running ldap_check.ps1 script from any joined computer
This script retrieves the timestamp from the domain controller – the other party’s version of events.
This is relatively easy to execute, just save into any machin connected to domain and save to a ps1 file, right click to run via ‘powershell’
#Determine the domain and computer's name
$ComputerName = Read-Host "Enter Computer Name"
$domain = (Get-WmiObject Win32_ComputerSystem).Domain
$filter = "(&(objectCategory=computer)(objectClass=computer)(cn=$ComputerName))"
$objectDN = ([adsisearcher]$filter).FindOne().Properties.distinguishedname
# get pwdlastset attribute modification date from ad object metadata
$pwdlastsetmetadata = "pwdlastset"
$context = new-object System.DirectoryServices.ActiveDirectory.DirectoryContext("Domain",$domain)
$dc = [System.DirectoryServices.ActiveDirectory.DomainController]::findOne($context)
$metadata = $dc.GetReplicationMetadata($objectDN)
$computerpwdchangetime = $metadata | %{$_.$pwdlastsetmetadata.LastOriginatingChangeTime}
$computerpwdchangetime = [DateTime]::SpecifyKind($computerpwdchangetime, [DateTimeKind]::Local)
$computerpwdchangetime = $computerpwdchangetime.ToUniversalTime()
$computerpwdchangetime = $computerpwdchangetime.ToString("yyyy-MM-dd hh:mm:ss")
# print to screen and save to file (change path if needed)
Write-Host -NoNewline "Password Last Set Time(UTC) in the AD Account object metadata`t: "
Write-Host -ForegroundColor Cyan $computerpwdchangetime
Set-Content -Path "c:\temp\pwdLastSet.txt" -Value ("Password Last set Time(UTC) in the AD Account object metadata " + $computerpwdchangetime)
Output analysis
Such as below is output txt in local machine:
Password Last Set Time (UTC) in the Local Machine secrets LSA 2025-02-11 05:56:53
and below is output for ldap timestamp:
Password Last Set Time (UTC) in the Local Machine secrets LSA 2025-02-11 05:56:53
When we compare these timestamps, we’ll encounter one of three scenarios:
- Perfect Harmony: Both timestamps match
- Everything is in sync
- No trust issues exist
- This is the ideal state we’re aiming for
- Living in the Past: Local timestamp is older
- Your machine is stuck in a time warp
- Usually happens after restoring from an old backup
- Most common scenario (like trying to use last year’s password)
- Future Shock: LDAP timestamp is older
- The domain controller needs attention
- Not a local machine issue
- Requires investigation of domain controller synchronization
Preventing Future Trust Issues
Remember Sarah from our opening story? She now keeps a local admin account handy and regularly checks her machine’s synchronization status. She learned that prevention is better than cure, especially when dealing with domain trust relationships.
Here are some best practices to maintain a healthy trust relationship:
- Regular backup verification
- Proper system restore procedures
- Monitoring domain controller health
- Maintaining current system timestamps
The Bottom Line
Domain trust relationships are like digital handshakes – they need to be firm and reliable. When they fail, it’s not just a technical hiccup; it’s a breakdown in communication between your machine and its digital community. By understanding the underlying causes and having a solid troubleshooting approach, you can turn this common IT headache into a manageable maintenance task.
Remember: In the world of domain relationships, trust is earned through synchronization, maintained through vigilance, and restored through understanding the underlying mechanics of what went wrong.
Have you encountered similar domain trust issues? How did you handle them? Share your experiences in the comments below – your story might help another IT professional in need!
#Windows #ActiveDirectory #ITTroubleshooting #TechSupport #SystemAdministration
–HTH–

